When Exposed API Keys Spill the Sensitive Data 😱😱

Hello readers! Recently, I teamed up with my friend Swapnil Bobale to work on a few bug bounty programs, and together, we discovered some amazing and unique vulnerabilities. We wanted to share the process we followed so that it might help you in your own bug-hunting journey. By walking you through the steps we took, we hope you can learn from our experience and find your own success.
As you might have guessed from the title, this vulnerability is all about API key exposure. I’ve noticed that many times, people simply find an API key and quickly report it as “API Key Disclosure.” But then, they get a response from the triager saying the vulnerability is “Not Applicable,” or the report gets marked as invalid. In some programs, it’s even mentioned that API key exposure is out of scope unless properly exploited.
So, in this article, we’ll talk about how to not just find an exposed API key but how to actually exploit it. I’ll walk you through the process so you can understand what makes the difference between a valid and an invalid report. Let’s dive in!

It all starts with Recon (Information Gathering). As we know, there are many ways to do Recon and Several Channels we can use to find sensitive information. One of the most effective methods is GitHub Recon. Many times, critical sensitive data is found on GitHub due to mistakes made by developers. That’s why, for this article, we’ll focus on GitHub recon as it often leads to valuable discoveries.
You know that moment when you’re mindlessly scrolling through GitHub, thinking, “What’s the worst that could happen?” Well, let me tell you, the worst did happen — and it’s not pretty. Picture this: Imagine leaving your house keys on a park bench with a note saying, “Hey, feel free to stop by anytime!” Well, someone did just that, except it wasn’t their house — it was their API! This key didn’t just unlock the front door; it unlocked the entire building! 🏢
You won’t believe where it was , It was like a treasure hunt, and the reward? Access to sensitive data. Yikes! 🎉
Now, don’t get too excited — no data was harmed in the making of this discovery! 🕵️♂️ We’re ethical, remember? But the potential for chaos was real.
What’s the Big Deal?
This innocent-looking API key allowed us to:
- Access private user data like accounts, forms, and histories.
- Update account settings (yes, we could’ve changed emails, websites, etc.).
- Perform CRUD operations (that’s hacker-speak for Create, Read, Update, Delete).
Basically, this key opened a digital back door to the house of sensitive data, and anyone with it could walk in like, “Honey, I’m home!” 🏠
Reproducing the Vulnerability
For all the readers in the back, here’s how we did it (don’t worry, I won’t give away too much!):
- We found the key hanging out in public GitHub repos (yep, you read that right 🤦♂️).

2. After finding the API key, the next step was to search for the API documentation. This helped us understand how the API works and gave us the curl commands we needed to fetch sensitive information.

curl -X GET "http://api.secretendpoint.com/user?apiKey=4dc975f640ce67e3967e6823fcda629b"This curl command revealed sensitive user details like account info, user folders, and even their history (and no, I don’t mean their embarrassing web searches — just API history). 😜
3. We tried some other curl commands like:
curl -X POST -d "email=hello@email.com" -d "website=www.newwebsite.com" "https://api.secretendpoint.com/user/settings?apiKey=4dc975f640ce67e3967e6823fcda629b"Yes, we could change account settings! (But no, we didn’t — we’re the good guys, remember?).
4. Lastly, we realized we could potentially wreak some CRUD havoc. Good thing we kept our white hats firmly on!
Proof of Concept (PoC)
I know what you’re thinking — SHOW ME THE RECEIPTS! 📸
Well, my fellow hunters, I’ve attached some juicy screenshots of the API documentation, the exposed key, and a handful of successful exploit images. If you’re interested in the full PoC’s, here’s a glimpse:
Trust me, the visuals will blow your mind! 🤯
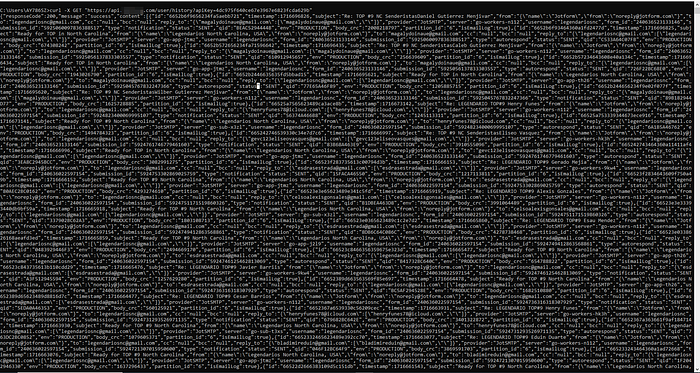
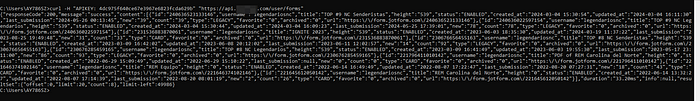

The Impact
Let’s talk about the mess this vulnerability could create if left unchecked:
- Unauthorized access to sensitive data — Imagine someone getting hold of your personal details and account settings!
- Account takeover — An attacker could change account emails, websites, and more. Ever wanted to mess with someone’s settings? Well, don’t. It’s bad!
- CRUD Operations — From creating to deleting, an attacker could be a silent, destructive guest in your API world. 👻
The Fix
Don’t worry, I’m not just here to point out flaws without helping clean them up. Here’s how we suggested they patch things up:
- Remove the exposed API key — Duh! That key should be more hidden than your high school diary.
- Restrict access to API documentation — Only those with a legitimate need should be able to see it, not the whole dang internet.
Conclusion
After weeks of searching for something fresh, my buddy and I finally got this unique finding. We were high-fiving like, “We still got it!” 😎 This just goes to show, the internet is a wild place full of surprises — you never know what you’ll stumble upon next.
Moral of the story: Always keep your API keys close and your hackers closer. And, if you’re feeling adventurous, GitHub might just have a treasure waiting for you.
We have got few more amazing vulnerabilities for which writeup is going to come soon. 😎
Let me know if you want me to make more tweaks or assist further!
You can Connect with me :-
Twitter:- https://twitter.com/imsushantkamble
Linkedin:- https://in.linkedin.com/in/iamsushantkamble
Facebook:- https://www.facebook.com/iamsushantkamble/
Kindly Give a Clap 👏 if you found this helpful and came across this kind of scenario.
